UMERCS BLOG
We Have a Problem (and Solution)
If you’ve read any headlines recently, you know that breaches are an unfortunate, yet common occurrence. You’re either numb to these notifications, or you’ve been asking: why and how does this keep happening?! Although there isn’t necessarily just one common reason, the overall problem is that of deterrence and discernment. Attackers select targets, e.g. your data, because they know their chances of getting caught are low. If they are caught, they know the cost to them (jail time, fines, reputation, etc.) is not very high. Finally, understanding how your adversary views your assets (data, systems, and even reputation) is a missing key component in prioritizing your defenses. Our goal is to change that.
We Have a Problem
If you’ve read any headlines recently, you know that breaches are an unfortunate, yet common occurrence. You’re either numb to these notifications, or you’ve been asking: why and how does this keep happening?! Although there isn’t necessarily just one common reason, the overall problem is that of deterrence and discernment. Attackers select targets, e.g. your data, because they know their chances of getting caught are low. If they are caught, they know the cost to them (jail time, fines, reputation, etc.) is not very high. Finally, understanding how your adversary views your assets (data, systems, and even reputation) is a missing key component in prioritizing your defenses. Our goal is to change that.
Our Solution: An Operationalized Active Defense
I am pleased to announce the formation of Traced. Traced is an answer to our adversary problem. This platform will empower individuals and organizations alike with the methodology and tool set to proactively annoy, attribute and interact with their adversaries. Put another way, we want to make you a hard target that causes your attacker to move on. As your adversaries adapt, so too will this platform. It will provide a means to identify adversaries early on, while providing enough attribution to take the appropriate action. Security is no longer a wait and see mentality. It needs to be proactive--an Active Defense.
Our Newest Member
Today I am also very excited to announce the platform’s Chief Technology Officer (CTO) and Chief Software Architect (CSA), Ryan McGeary!
Traced CTO & CSA
Welcome Ryan!
Ryan is a serial entrepreneur, software consultant, international speaker, and amateur triathlete. Ryan has 20 years of experience developing both business and consumer software products and is a global speaker on emerging web development technologies and processes. Ryan co-founded other companies such as BusyConf, ChargeStack, LMGTFY, FitFreak, SplashWireless and McGeary Consulting Group. He is a graduate of the University of Virginia with a degree in Computer Science and an emphasis in Economics.
Ryan brings a wealth of coding experience to the table and I will be eager to show off his talents via this platform!
In Case You Missed It
uMercs was recently featured as a guest writter on AlienVault’s blog. Head on over and check it out!
Ethereum Denver: How to Monitor a Network on the Fly
uMercs has the unique opportunity to support the security and networking for the ETHDenver Hackathon. This post dives into this hot topic that is blockchain and how you can do your own Network Security Monitoring (NSM) on the fly and other lessons learned.
About a month ago, I was presented with a unique network and security challenge. A friend of mine asked me to be part of a hackathon in the local area dubbed ETHDenver. Specifically, he was asking me to help support the network and security monitoring during the conference. My first question was: what is ETHDenver? If you’re involved in any cryptocurrency, you’ve probably heard of Ethereum. ETHDenver is a new event in the Denver Colorado area that brings together some of the foremost blockchain researchers, entrepreneurs, businesses, artists and coders the world over. In some regards, it was a “choose-your-own-destiny” event. Some were there to just be part of the hackathon, where others were there to hear the various speakers. More on the hackathon in a few but suffice it to say is that our challenge was to setup, support, and monitor the network and security of that network for over 3000+ individuals over the course of 3 days. One of the biggest lessons learned for me, was that the blockchain has immense capability beyond just cryptocurrencies.
Figure 1. ETHDenver Hackathon, February 16 - 18, 2018
Figure 2. Ethereum Artwork.
The Block Chain: Much More than Crypto Currencies
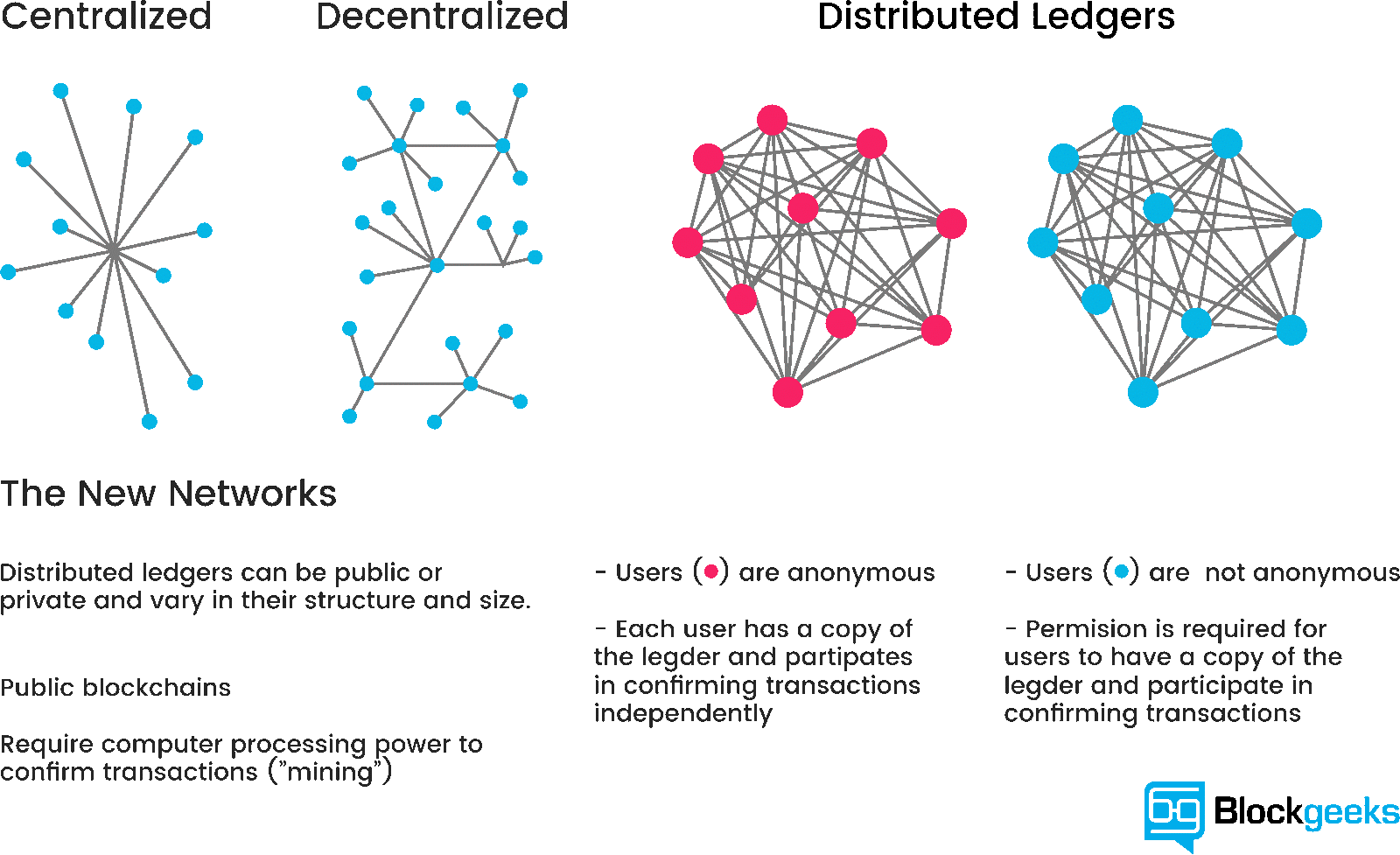
When I talk to people about the blockchain, Bitcoin is typically referenced and rightfully so. Bitcoin is the leading crypto currency that operates via a blockchain. There are more crypto currencies than you can shake a stick at and all promise some differentiating factor. At ETHDenver, the focus was on the Ethereum block chain. According to the Ethereum website, Ethereum is a decentralized platform that runs smart contracts: applications that run exactly as programmed without any possibility of downtime, censorship, fraud or third-party interference. These apps run on a custom built blockchain, an enormously powerful shared global infrastructure that can move value around and represent the ownership of property. Blockgeeks provides a great background on the blockchain in simple terms if you’re looking for a more detailed explanation. Figure 2 illustrates what the distributed ledger looks like as compared to a centralized or decentralized model. Ethereum’s claim to fame is the smart contract and ETHDenver was all about how that contract can be used in innovative ways, other than just cryptocurrencies. That was what the event was all about and the focus of the hackathon.
Figure 2. Blockgeeks Illustration of the Different Network Types.
The Hackathon
As a security professional, the thought of a hackathon usually entails a weekend of caffeine, exploits, and the painful persistence of trying to compromise a target system. But hacking is so much more than just computer hacking, as you may already know. In the context of the event, this hackathon was about hacking code together to achieve your desired goal of leveraging the blockchain for a novel function. At the end of the weekend, seven winners were announced out of hundreds who participated. The seven winners all had varying uses for the blockchain. From a security and infrastructure perspective, the one that stood out to me was a project dubbed Canteen. It was touted as a decentralized container orchestrator. Possibly put another way: a peer-to-peer self-healing container network. If one node were to go down, the “stack” could be simply be rebuilt from a trusted peer in the blockchain, minimizing downtime. If only we had that for the internet connection…
Monitoring Challenges and Other Woes
With a large conference, and especially a tech conference, there will be issues. I think that might be a universal law somewhere. The first challenge was that of time. Little time was provided to get infrastructure and security monitoring in place. With about a two-week window to work in, Internet, wireless infrastructure and security monitoring were needed. Thankfully, the internet circuit was ordered and delivered prior to the event. The wireless Access Points (APs) of choice were Cisco Meraki. With 3000+ users, there were approximately 45 APs in use at the Denver infamous Sports Castle.
The other area that required attention was network security monitoring (NSM). Based on our time and options, we opted to use USM Anywhere, by AlienVault. If you’re unfamiliar with this platform, it is essentially a Cloud hosted version of the USM Appliance. The main UI is hosted and the sensors are deployed on site. This setup permitted NSM for the local network via the sensor and a centralized view into the traffic from virtually anywhere. We ended up setting up a SPAN port of the switch where all of the wireless traffic eventually traversed. That traffic was sent to the USM sensor. USM Anywhere permitted the monitoring of the network from other locations and not just from the physical conference location. All in all, the setup was a breeze and it took less than about an hour to get up and running (plus or minus a few minutes to download the on-site sensor). Figure 3 illustrates the USM UI dashboard.
Figure 3. The Main UI for USM Anywhere
Finally, the largest challenge that plagued day one was that of an Internet outage. It was eventually solved, but due to network congestion and faulty business class cable modems, we had our work cut-out for us. True to the distributed blockchain nature of the conference, we ended up having to further segment the networks, on the fly, via dedicated cable modems (as seen in figure 4).
Figure 4. Distributed Cable Modems to Deal with Faulty Hardware (not exactly recommended, but hey).
It wouldn’t be complete if I didn’t mention that some of the alerts we received via USM was Ethereum traffic (figure 5).
Figure 5. Ethereum Traffic Alerts via USM.
Deception to Add Context
As an added area of research, I ended up deploying two instances of MazeRunner Community Edition. For my own edification, but also because in an untrusted network, it was an area to help with early detection of nefarious behavior. Essentially, this technology was deployed to various segments of the network and acted much like a high-interaction honeypot. The alerts from the system were directed to the USM sensor, which allowed for centralized monitoring. Aside from scanning, no one seemed to want to discover more about these systems—probably too focused on hacking some code together.
Observations and Conclusion
All that said, here are some of the takeaways and things to think about if you’re ever in a position where you need to provide similar services for a hackathon or other conference:
- Plan appropriately for bandwidth (both Internet and wireless). If 2.4 GHz is not needed, consider forcing clients to use 5GHz for quicker speeds.
- Have a back-up internet connection and especially if the conference is doing live streaming.
- Ensure your network can be monitored from a utilization and security perspective.
- Incident Response looks a lot different on an untrusted network. Knowing if something is up being a big priority (via NSM and possibly deception technology). Being able to ban or restrict an end user might be your only defense or containment option.
- Setting up secure remote access helps un-tether you from the physical conference location.
Overall, it was a great learning experience and one way to give you confidence in your abilities. From my perspective, it was also great to learn about new and emerging technology, but that’s what it’s all about, isn’t it?
How Are Your Adversaries Motivated?
According to this infamous manifesto, all hackers are alike and not unique millennial snowflakes. They are people with curiosity, convictions, apathy, anger, greed, hope, and honor. Just like people, hackers or groups of hackers may fall on a spectrum of good and evil. Where they fall may be dependent on the day or mood of that individual, or even the convictions of the larger collective.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me for.
I am a hacker, and this is my manifesto. You may stop this individual, but you can't stop us all... after all, we're all alike. –The Conscience of a Hacker From Phrack Magazine 1986, The Mentor
According to this infamous manifesto, all hackers are alike and not unique millennial snowflakes. They are people with curiosity, convictions, apathy, anger, greed, hope, and honor. Just like people, hackers or groups of hackers may fall on a spectrum of good and evil. Where they fall may be dependent on the day or mood of that individual, or even the convictions of the larger collective. For example, the collective Anonymous was a way for anyone, and I mean anyone, to be involved in hacking for an ideal if you so desired. Hate oil and gas? There was an operation for that. How about the stock market? There was Occupy Wall Street for that. What about nation states or organized crime? They might be hackers under the hood, but their motives might be considered malformed by some. On the flip side, hackers work to bring job training and technology to areas of the world that are so impoverished, they would not be able to do so on their own.
Defining Your Adversary
So maybe that’s the problem: labeling hackers as bad or good. Maybe it’s more specific than that. If you’re reading this, you’re probably wondering what the motives are behind the “bad” hackers of the world. The media does a great job classifying all hackers as bad and their motives as evil. Truly, a “bad” hacker, is subjective. To understand a bad hacker’s motives, it is more important to understand who your adversaries are. This is an important differentiator for two reasons:
- An adversary implies that there is someone/somebody who has a problem with you and your organization specifically.
- An adversary helps you to understand a motive and the targets they are after.
Forming this background is one method in understanding an adversary’s motives and even the endgame.
A Motive Breeds the Target
A common question is often sought by law enforcement. What was the motive? This is typically to point the investigators to the why, which can help to uncover more information or evidence to support the case and why the victims were targeted. Similarly, finding the why, or motive, behind your adversary’s actions can help you better understand what they are after and how to protect those assets from an attack. Take the following motives as an example:
- Financial: Can the adversary make money directly (via an attack) or indirectly (by selling malware or ransomware as a service)? Are their competitors who may want to destabilize your company?
- Ideological: You adversary may want to harm your reputation, deny services to your customers, or sabotage your systems in order to further their propaganda or eliminate perceived threats to the environment, for example This could also include frustrated ex-employees.
- Political: Can the adversary benefit from knowing your next move or most intimate secrets as an organization? Do you claim that you have impenetrable defenses? If so, you might be motivating an attacker to find a way in.
- Prestige and Curiosity: Does the adversary want to say they compromised your organization just because? Do you have such an interesting technological footprint so enticing to an attacker?
These common motives will help you and your organization realize what could be a target and focus your budget and resources at the most vulnerable areas
All Motives Not Equal
Financial motives are among the largest reasons for targeting an organization or individual. According to estimates by Juniper Networks, the cost of data breaches will soar to $2.1 trillion dollars by 2019. This staggering statistic signals that there is money to be made. An investigative tool called Hunchly, offers a service that searches the dark web and reports its findings on a daily basis.
Crime is a commodity because it pays. Furthermore, an organization that may not be a target for one adversary, will be one for another. Simply put, if you do not make yourself a hard target, it is only a matter of time before your organization is caught in the cross-hairs.
What is the Target?
If your adversary is financially motivated, they will more than likely be after data that can be bought and sold. In the case of ransomware, they might be after the data that you need to run your business knowing you will pay anything to get it back. A recent malware outbreak, dubbed “Bad Rabbit”, is one example where the authors were after a ransom. The target: Russian media outlets and other large corporate networks. These targets were presumably chosen because of the propensity to pay the ransom. If attackers have ideological goals, they might be looking to deny services or deface an organization’s publicly facing systems. Not knowing who your adversary is and what is motivating them is like trying to plan for a trip without knowing what the weather will be like when you get there. That translates into needing to prepare for every occasion, which is time consuming, expensive, and nearly impossible.
Conclusion
Do you know who is targeting you and why? What are they after? These questions should be at the forefront of your mind and cybersecurity planning. Not only will this view help you look at what you’re trying to protect from the adversary perspective it will help align your strategy to meaningful priorities. When in doubt follow the money. When you’re informed, prioritize your defenses on the motives of your adversaries.